Trend Micro has discovered a new malicious campaign that is targeting individuals in the Eastern European cryptocurrency industry through a fake employment ploy.
According to the report, Russian hackers are behind this campaign use highly obfuscated and underdeveloped custom loaders to infect their targets with the Enigma stealer (also known as TrojanSpy.MSIL.ENGIMASTEALER.YXDBC), which is a modified version of the information stealer Stealerium.
The attackers also leverage a vulnerability (CVE-2015-2291) in an Intel driver to load a malicious driver that weakens the token integrity of Microsoft Defender.
Enigma Stealer is a modified version of the original information stealer, Stealerium. Stealerium is an open-source project written in C# that claims to be a stealer, clipper, and keylogger with the ability to log information using the Telegram API.
How Dose The Attack Work?
The attack begins with an email impersonating a job offer with fake cryptocurrency interviews, meant to lure in the target. The email comes with a RAR archive attachment that contains two files: “interview questions.txt” and “interview conditions.word.exe”. The text file contains interview questions written in Cyrillic that seem genuine and follow a typical format.
Should the victim fall for the trap and run the executable, a series of payloads will be executed, ultimately resulting in the downloading of the Enigma stealer malware from Telegram.
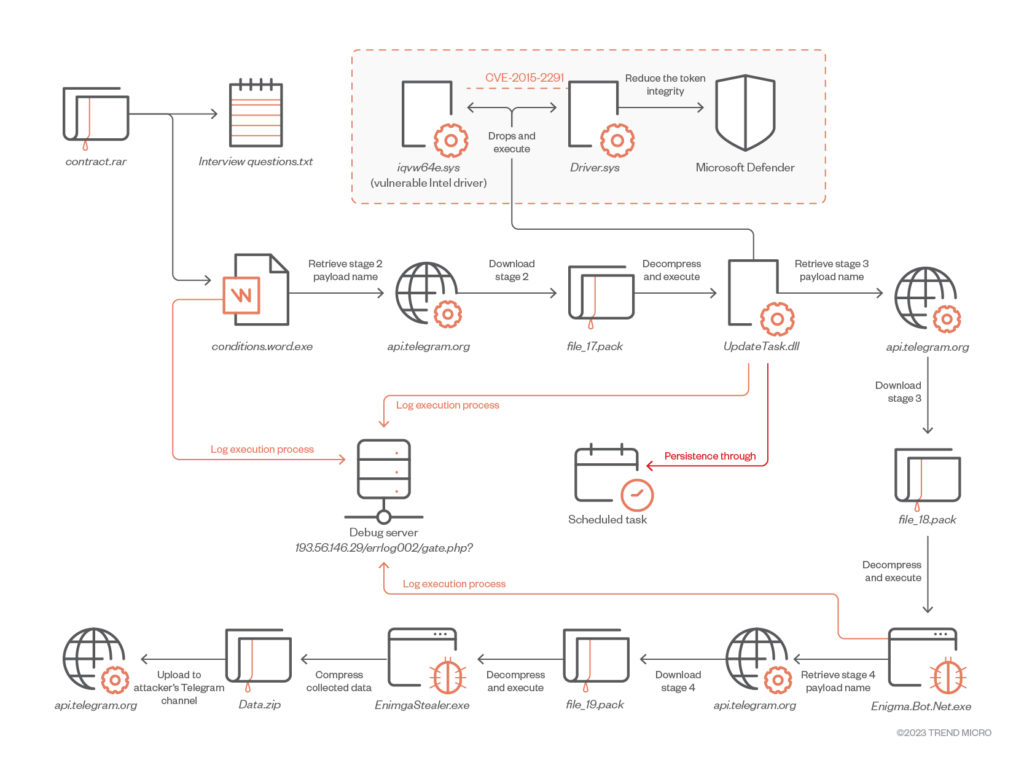
The initial downloader, written in C++, employs techniques such as API hashing, string encryption, and irrelevant code to evade detection while downloading and launching the second-stage payload, known as “UpdateTask.dll”.
The second-stage payload, also written in C++, employs the “Bring Your Own Vulnerable Driver” (BYOVD) technique to exploit the Intel vulnerability CVE-2015-2291. This vulnerability in the Intel driver allows for commands to be run with kernel-level privileges.
The cybercriminals exploit this weakness to turn off Microsoft Defender before downloading the third payload, which is the actual malware.
















+ There are no comments
Add yours