Lazarus hacking group, suspected to be linked to North Korea, has been discovered exploiting a previously unknown vulnerability (Zero-Day) in Microsoft Windows based systems to stealthily gain kernel-level access on target systems. According to an analysis published by Avast, the group is leveraging this access to deploy an advanced rootkit designed to disrupt security products and evade detection.
The vulnerability, now patched as CVE-2024-21338, exploits Windows AppLocker driver (appid.sys). That enabled The Lazarus group cleverly exploited this vulnerability, allowing them to gain kernel-level access on compromised systems, giving the attacker complete control over the system’s core functionalities.
The latest Avast’s investigation report revealed an updated variant of Lazarus group’s FudModule rootkit. Four techniques in the latest FudModule version are completely new, while three others have been updated for enhanced effectiveness, the new version of FudModule rootkit relies on manipulating kernel data structures to disable security mechanisms like registry callbacks, object callbacks, and process/thread/image notifications.
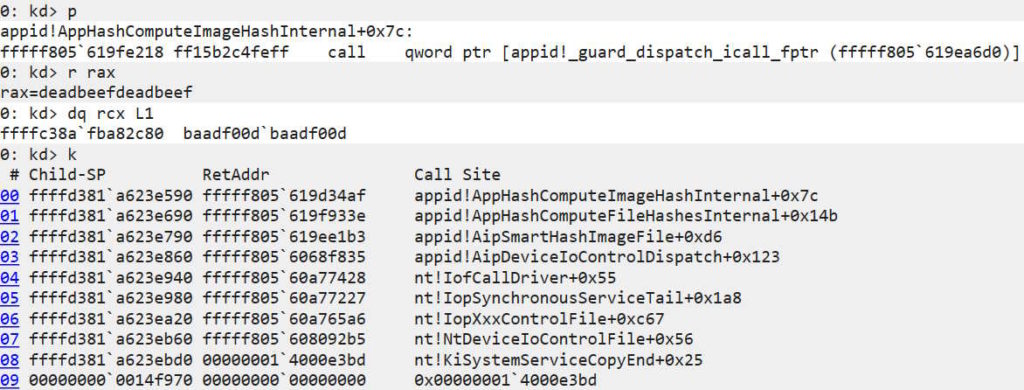
The rootkit specifically targets functionality used by antivirus and endpoint detection solutions to monitor system activity. Notably, Lazarus employed a new handle table entry manipulation technique to suspend Protected Process Light (PPL) protected processes associated with security solutions like Microsoft Defender and other security software like CrowdStrike Falcon and HitmanPro.
The use of an admin-to-kernel exploit like CVE-2024-21338 takes Lazarus’ hacking operations to the next level compared to past campaigns. Previously, the group relied on noisier Bring-Your-Own-Vulnerable-Driver (BYOVD) techniques that exploited third-party drivers. The use of a zero-day exploit instead shows the group’s commitment to stealthy, long-term persistence on compromised networks.
The Lazarus hacking group, believed to be sponsored by North Korea. Active since at least 2009, Lazarus has gained global attention for its audacious and highly sophisticated attacks targeting various sectors, including finance, cryptocurrency exchanges, government, and critical infrastructure
Recent major campaigns have seen Lazarus hack several cryptocurrency exchanges and steal over $100 million in digital assets last year alone [1]. The group also continues targeting security researchers through elaborate social engineering tactics [2], likely in an attempt to impede analysis of its malware. Most recently, Lazarus was observed exploiting a Windows zero-day vulnerability to covertly install an advanced rootkit on compromised systems [3]. This allows the group to disable security services and hide malicious activity, highlighting its interest in stealthy long-term access. While primarily targeting South Korea [4], Lazarus has been known to hit other Asia Pacific targets and launch indiscriminate ransomware campaigns against Western organizations [5]. With sizable resources and a diversity of attack vectors, Lazarus remains a highly sophisticated and persistent cyber threat.