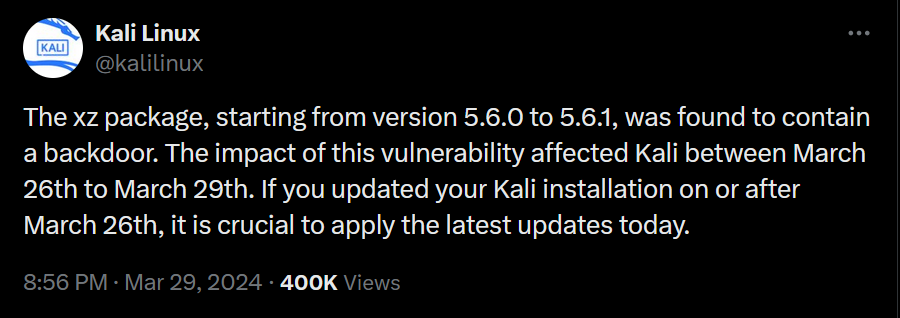
RedHat issued a security alert about a critical supply chain compromise affecting the widely used data compression library, XZ Utils (formerly known as LZMA Utils).
The XZ package, starting from version 5.6.0 to 5.6.1, was found to contain a backdoor CVE-2024-3094.
The newly discovered backdoor hijacks the OpenSSH server daemon to enable remote code execution and unauthorized system access under certain conditions. While no active exploitation has been spotted yet, the potential for a complete system takeover is deeply concerning.
What is XZ Utils ?
XZ Utils (AKA LZMA Utils) is a set of free software and open source command-line , commonly used and available for most, if not all, Linux distributions. However, it is not included by default in all of them. Some Distributions may ship with XZ Utils pre-installed like Kali Linux, others require manual installation. If you’re unsure whether it’s installed on your system, you can check and install it using package managers like yum or apt.
How to check if my system is vulnerable to CVE-2024-3094 backdoor?
You can check if XZ Utils is installed on your Linux system and using one of the following methods:
1- Using the command line:
Run the bellow XZ version command on your Linux terminal:
xz --version
Here is what the output of a CVE-2024-3094 vulnerable version may look like:
$ xz --version
xz (XZ Utils) 5.6.1
liblzma 5.6.1
You can proceed with further actions based on the version you have.
2- Using a script:
You can use CVE-2024-3094-checker script on GitHub to quickly check whether your system contains a vulnerable version of XZ Utils:
wget https://github.com/FabioBaroni/CVE-2024-3094-checker/blob/main/CVE-2024-3094-checker.sh
chmod +x CVE-2024-3094-checker.sh
./CVE-2024-3094-checker.sh
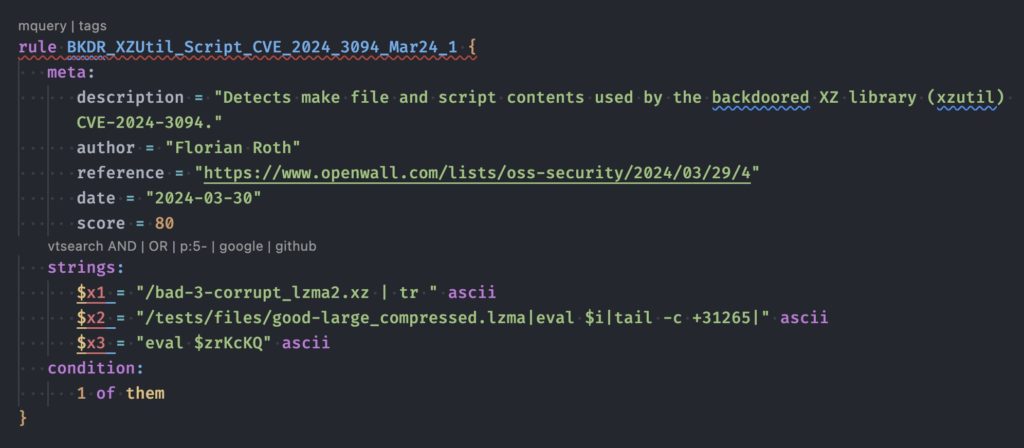
3- Using Lara Rules
You may also test your system using the set of free YARA rules to detect the backdoored XZ packages.
Current Vulnerable Linux Distros:
Here are the Linux distributions where it is likely to be patched (according to repology):
- Alpine Edge
- Arch
- Cygwin
- Exherbo
- Gentoo
- Homebrew
- KaOS
- MacPorts
- Manjaro Testing
- NixOS Unstable/nixpkgs unstable
- OpenIndiana
- OpenMamba
- OpenMandriva Rolling
- Parabola
- PCLinuxOS
- Pisi Linux
- pkgsrc current
- Ravenports
- Slackware current
- Solus
- Termux
- Wikidata
How this was discovered?
Microsoft security researcher Andres Freund has been credited with discovering and reporting the issue on Friday. The heavily obfuscated malicious code is said to have been introduced over a series of four commits to the Tukaani Project on GitHub by a user named JiaT75.












