Ransomware group Hunters International has quietly shut down its operations. In a surprising move, the gang deleted all stolen data from its leak site and offered free decryptors to victims. The announcement was shared on their dark‑web portal on July 3, 2025. It marked the end of a nearly two year run that began in late 2023.
On July 3, 2025, Hunters International posted a note on its exclusive leak site. They said recent developments—though unspecified—led them to close the project “after careful consideration.” They deleted everything: all victim listings and data entries. And to prove sincerity, they offered decryptors to every victim, saying their goal was to help organizations regain access to encrypted files without paying a ransom.
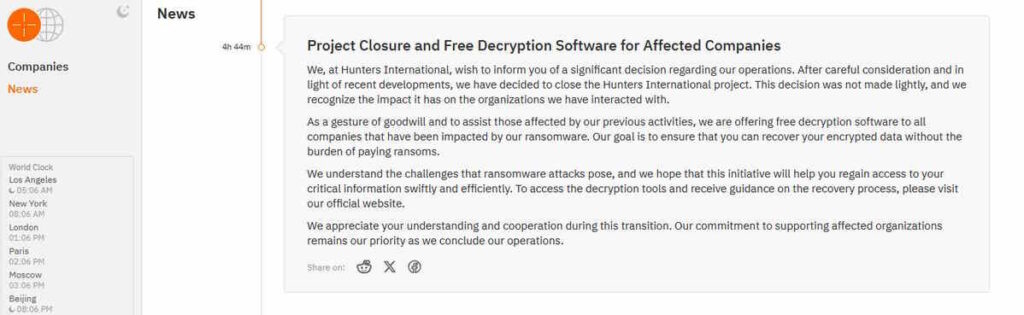
It was a rare gesture. Ransomware groups don’t usually do this. The last known example was Avaddon in 2021—then the group rebranded as NoEscape.
Why it matters?
The shutdown is more than a news story. Hunters International was among the most active and dangerous ransomware gangs in 2024–2025:
- They claimed nearly 300 attacks worldwide.
- They hit hospitals, manufacturing, finance, government, and education. Notable targets include the Hoya Corporation, U.S. Marshals Service, Fred Hutch Cancer Center, Tata Technologies, AutoCanada, and Integris Health.
- One of the Fred Hutch attacks threatened 800 000 patients’ data.
- Hunters International had ties to the collapsed Hive ransomware group, with code overlap and shared affiliates. Hunters claimed to have purchased Hive’s source code.
Hunters International’s encrypting tools covered all major platforms such as Windows, Linux, FreeBSD, SunOS, ESXi, with x86/64 and ARM support, in Rust code. They used double‑extortion: encrypt files, steal data, and threaten leaks.
Free decryptors: real or a trap?
Victims can now request decryptors from the Hunters site. But there are warning signs. Security analysts say the tools may be poorly built. It may even be a trap to infect systems with more malware .
Experts from Emsisoft, Sophos, and SANS urge caution:
- Verify the code in a secure environment first.
- Sandbox the decryptor before using it on live systems.
- Independent security firms should vet the tool before widespread use.
Still, this might be the only chance for some affected organizations to recover data.
But don’t be fooled: rebrand likely
The consensus is that this shutdown is not genuine closure. Analysts from Group‑IB, CyberInsider, Risky Business, CSO Online, InfoSecurity, and GovInfoSecurity all warn that Hunters is rebranding, not going away.
If your organization has been hit by Hunters
- Confirm ransomware identity. Check ransom notes and file extensions (e.g., “.LOCKED”) for connection to Hunters.
- Back up encrypted data before testing any decryptor.
- Use a sandbox or isolated environment to test the decryptor.
- Engage a third party or CERT to analyze the tool. Don’t trust blindly.
- Monitor World Leaks for any exposure of your data.
- Update defenses: patch servers, reinforce backups, train staff, use MFA, deploy EDR/XDR tools, and threat‑hunt for exfil tools like Storage Software.