Evasive Panda (also known as BRONZE HIGHLAND and Daggerfly), Chinese-speaking APT groups, are targeting Tibetans through strategic web compromises (watering hole attacks) and supply-chain compromises.
These cyberespionage campaigns aim to deliver trojanized installers of Tibetan language translation software, which in turn could compromise website visitors with MgBot and a backdoor called Nightdoor. Nightdoor is not publicly documented yet, so it’s an unknown threat in the wild.
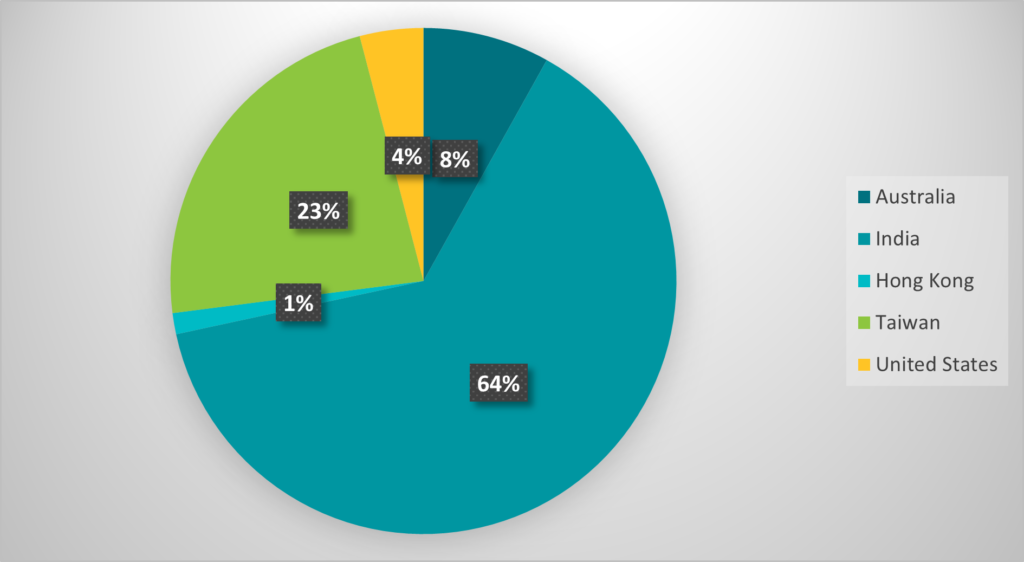
According to a recent published ESET researchers report, Evasive Panda, the group behind this campaign, has been active since at least 2012 and targets individuals and organizations across mainland China, Hong Kong, Macao, and Nigeria. They’ve also shown interest in entities in India, Malaysia, and other regions.
The group uses its own custom malware framework with a modular architecture that allows its backdoor to receive modules to spy on victims and enhance its capabilities. Evasive Panda can also deliver its backdoors via adversary-in-the-middle attacks that hijack legitimate software updates.
In January 2024, ESET researchers discovered a cyberespionage operation that compromised at least three websites to carry out watering hole attacks and a supply-chain compromise of a Tibetan software company. One such website was Kagyu International Monlam Trust, which promotes Tibetan Buddhism internationally. The attackers took advantage of this site to place a script that directed potential victims to a malicious downloader if their IP address fell within the targeted ranges. This tactic is designed to take advantage of users interested in the annual Kagyu Monlam Festival held in India.
Another key part of this operation was the compromise of an Indian software development company specializing in Tibetan language translation software. The attackers placed several trojanized applications on this site, which then led users to malicious downloaders for Windows and macOS once installed. Furthermore, the attackers also abused both the compromised website and a Tibetan news website called Tibetpost to host the payloads obtained by the malicious downloads.
Advanced Persistent Threat (APT) groups are highly talented hacking groups that typically operate with long-term objectives. They usually use various hacking techniques to gain and maintain permanent access to a target’s network, often remaining undetected for extended periods. The most well-known APT group is likely APT28, also known as Fancy Bear or Tsar Team, which has been linked to Russian intelligence services since at least 2006.












