Security researchers at Kaspersky are tracking a malware campaign that targets ebook readers across several regions. The attack was reported and documented by Kaspersky’s Global Research and Analysis Team.
The attackers hide malware inside files that look like popular Turkish and Arabic books and People searching for free ebooks end up downloading these infected files instead.
How The Attack Works?
The files appear as best sellers titles PDF ebooks. The files have PDF icons, but in reality these files are not documents PDF files. They are executable programs.
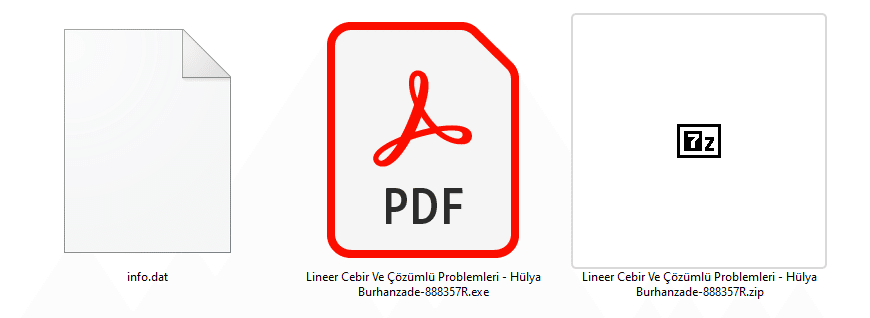
Once opened, the file runs a loader called LazyGo. LazyGo is written in Go and works as part of a malware-as-a-service setup, its sole purpose is to drop more malware on the victim’s system.
This attack is targeting users in Turkey, Egypt, Bangladesh and Germany. Affected sectors range from government and education to IT services.
Turkish and Arabic Users Are Targeted
The campaign targets readers looking for well-known titles. These include Turkish translations of classic novels, business books, and modern fiction. Arabic content is also used, such as poetry, folklore, religious texts, and literary studies.
After execution, LazyGo installs information-stealing malware. Kaspersky observed StealC, Vidar, and ArechClient2 being delivered this way.
LazyGo Variants
Researchers found three LazyGo variants in the wild. Each one uses different tricks to avoid detection.
These include AMSI bypass, API unhooking, ETW disabling, and checks for virtual machines.
Attackers collect saved passwords, cookies, autofill data, and browsing history, crypto wallets private keys, configuration files, and local storage.
The malware looks for cloud credentials such as AWS credentials, Azure CLI tokens, and Microsoft identity tokens, social apps data such as Discord tokens, Telegram Desktop data, and Steam session files are harvested.
System data is collected as well.
The maleware will also hardware details, installed software, system info, local files list, and running processes.
In cases where another malware tool ArechClient2 is deployed, the risk is higher, as attackers gain full remote access to the infected machine.
Kaspersky Says the Operation is Not Random.
According to Yossef Abdelmonem, Senior Security Researcher at Kaspersky GReAT, the campaign shows clear planning. The use of MaaS (Maleware-As-A-Service) , multiple loader variants, and targeted lures points to a structured effort. Stolen cloud and developer credentials can be used to access inside organizations.
The campaign is still active.